文件上傳漏洞php代碼有哪些-創新互聯
這篇文章給大家介紹文件上傳漏洞php代碼有哪些,內容非常詳細,感興趣的小伙伴們可以參考借鑒,希望對大家能有所幫助。
創新互聯公司專注于企業網絡營銷推廣、網站重做改版、井研網站定制設計、自適應品牌網站建設、成都h5網站建設、商城網站開發、集團公司官網建設、成都外貿網站建設、高端網站制作、響應式網頁設計等建站業務,價格優惠性價比高,為井研等各大城市提供網站開發制作服務。漏洞描述
開發中文件上傳功能很常見,作為開發者,在完成功能的基礎上我們一般也要做好安全防護。
文件處理一般包含兩項功能,用戶上傳和展示文件,如上傳頭像。
文件上傳攻擊示例
upload.php
<?php
$uploaddir = 'uploads/';
$uploadfile = $uploaddir . basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)){
echo "File is valid, and was successfully uploaded.\n";
}
else {
echo "File uploading failed.\n";
}
?>upload.html
<form name="upload" action="upload1.php" method="POST" ENCTYPE="multipart/formdata"> Select the file to upload: <input type="file" name="userfile"> <input type="submit" name="upload" value="upload"> </form>
上述代碼未經過任何驗證,惡意用戶可以上傳php文件,代碼如下
<?php eval($_GET['command']);?>
惡意用戶可以通過訪問 如http://server/uploads/shell.php?command=phpinfo(); 來執行遠程命令
Content-type驗證
upload.php
<?php
if($_FILES['userfile']['type'] != "image/gif") {//獲取Http請求頭信息中ContentType
echo "Sorry, we only allow uploading GIF images";
exit;
}
$uploaddir = 'uploads/';
$uploadfile = $uploaddir.basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)){
echo "File is valid, and was successfully uploaded.\n";
} else {
echo "File uploading failed.\n";
}
?>該方式是通過Http請求頭信息進行驗證,可通過修改Content-type ==> image/jpg繞過驗證,可以通過腳本或BurpSuite、fiddle修改
如下
Content-Disposition: form-data; name="userfile"; filename="shell.php"
Content-Type: image/gif
圖片類型驗證
該方法通過讀取文件頭中文件類型信息,獲取文件類型
備注:如JPEG/JPG文件頭標識為FFD8

upload.php
<?php
$imageinfo = getimagesize($_FILES['userfile']['tmp_name']);
if($imageinfo['mime'] != 'image/gif' && $imageinfo['mime'] != 'image/jpeg') {
echo "Sorry, we only accept GIF and JPEG images\n";
exit;
}
$uploaddir = 'uploads/';
$uploadfile = $uploaddir . basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)){
echo "File is valid, and was successfully uploaded.\n";
} else {
echo "File uploading failed.\n";
}
?>可以通過圖片添加注釋來繞過此驗證。
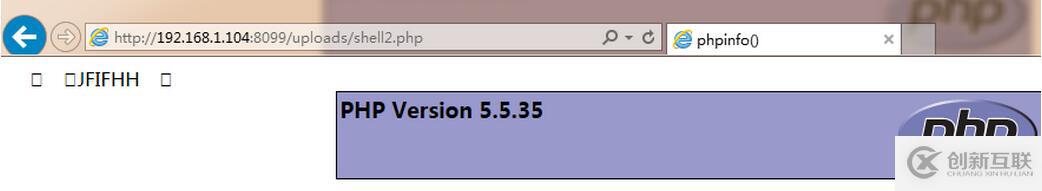
如添加注釋<?php phpinfo(); ?>,保存圖片后將其擴展名改為php,則可成功上傳。
上傳成功后訪問該文件則可看到如下顯示
文件擴展名驗證
通過黑名單或白名單對文件擴展名進行過濾,如下代碼
upload.php
<?php
$blacklist = array(".php", ".phtml", ".php3", ".php4");
foreach ($blacklist as $item) {
if(preg_match("/$item\$/i", $_FILES['userfile']['name'])) {
echo "We do not allow uploading PHP files\n";
exit;
}
}
$uploaddir = 'uploads/';
$uploadfile = $uploaddir . basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)){
echo "File is valid, and was successfully uploaded.\n";
} else {
echo "File uploading failed.\n";
}
?>當黑名單不全,構造特殊文件名可以繞過擴展名驗證
直接訪問上傳的文件
將上傳文件保存在非web root下其他文件夾下,可以防止用戶通過路徑直接訪問到文件。
upload.php
<?php
$uploaddir = 'd:/uploads/';
$uploadfile = $uploaddir . basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)) {
echo "File is valid, and was successfully uploaded.\n";
} else {
echo "File uploading failed.\n";
}
?>用戶不可以直接通過http://localhost/uploads/ 來訪問文件,必須通過view.php來訪問
view.php
<?php $uploaddir = 'd:/uploads/'; $name = $_GET['name']; readfile($uploaddir.$name); ?>
查看文件代碼未驗證文件名,用戶可以通過例如http://localhost/view.php?name=..//php/upload.php,查看指定的文件
解決漏洞示例
upload.php
<?php
require_once 'DB.php';
$uploaddir = 'D:/uploads/';
$uploadfile = tempnam($uploaddir, "upload_");
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)) {
$db =& DB::connect("mysql://username:password@localhost/database");
if(PEAR::isError($db)) {
unlink($uploadfile);
die "Error connecting to the database";
}
$res = $db->query("INSERT INTO uploads SET name=?, original_name=?,mime_type=?",
array(basename($uploadfile,basename($_FILES['userfile']['name']),$_FILES['userfile']['type']));
if(PEAR::isError($res)) {
unlink($uploadfile);
die "Error saving data to the database. The file was not uploaded";
}
$id = $db->getOne('SELECT LAST_INSERT_ID() FROM uploads');
echo "File is valid, and was successfully uploaded. You can view it <a href=\"view.php?id=$id\">here</a>\n";
} else {
echo "File uploading failed.\n";
}
?>view.php
<?php
require_once 'DB.php';
$uploaddir = 'D:/uploads/';
$id = $_GET['id'];
if(!is_numeric($id)) {
die("File id must be numeric");
}
$db =& DB::connect("mysql://root@localhost/db");
if(PEAR::isError($db)) {
die("Error connecting to the database");
}
$file = $db->getRow('SELECT name, mime_type FROM uploads WHERE id=?',array($id), DB_FETCHMODE_ASSOC);
if(PEAR::isError($file)) {
die("Error fetching data from the database");
}
if(is_null($file) || count($file)==0) {
die("File not found");
}
header("Content-Type: " . $file['mime_type']);
readfile($uploaddir.$file['name']);
?>上述代碼文件名隨機更改,文件被存儲在web root之外,用戶通過id在數據庫中查詢文件名,讀取文件,可以有效的阻止上述漏洞發生
通過以上示例分析,可總結一下幾點
1.文件名修改,不使用用戶上傳的文件名
2.用戶不可以通過上傳路徑直接訪問文件
3.文件查看采用數據庫獲取文件名,從而在相應文件服務器讀取文件
4.文件上傳限制文件大小,個人上傳數量等
關于文件上傳漏洞php代碼有哪些就分享到這里了,希望以上內容可以對大家有一定的幫助,可以學到更多知識。如果覺得文章不錯,可以把它分享出去讓更多的人看到。
網頁標題:文件上傳漏洞php代碼有哪些-創新互聯
轉載來于:http://www.yijiale78.com/article22/ccdjjc.html
成都網站建設公司_創新互聯,為您提供Google、品牌網站制作、網站導航、外貿建站、搜索引擎優化、商城網站
聲明:本網站發布的內容(圖片、視頻和文字)以用戶投稿、用戶轉載內容為主,如果涉及侵權請盡快告知,我們將會在第一時間刪除。文章觀點不代表本網站立場,如需處理請聯系客服。電話:028-86922220;郵箱:631063699@qq.com。內容未經允許不得轉載,或轉載時需注明來源: 創新互聯

- 什么是服務器?服務器托管與租用有什么不同? 2022-10-03
- 新時代|服務器托管應具備的優勢有哪些? 2021-03-17
- 哪家四川服務器托管便宜?成都托管服務器費用每年要多少錢? 2023-02-02
- 為什么服務器托管比租用費用高? 2021-03-11
- 服務器租用、服務器托管、云服務器:哪個適合你 2021-03-02
- 服務器托管與虛擬主機租用有什么區別? 2022-06-19
- 服務器托管收費標準一般是多少? 2022-10-09
- 為何服務器托管成為企業的首選? 2022-10-05
- 服務器托管的好處和優勢 2022-10-13
- 為什么要把服務器托管到IDC機房? 2021-03-16
- 服務器托管/租用和虛擬主機的區別,不能不看的網站知識 2021-02-11
- 為什么要進idc數據中心服務器機房托管? 2015-03-10